The history of consensusConsensus An agreement among blockchain participants on the validity of transactions. It is a key concept, essential for ensuring that all nodes on a chain share the same information. mechanisms begins with a fundamental problem in computer science: the Byzantine generals problem.
Imagine several generals who must coordinate an attack but can only communicate through messengers. Some generals may be traitors, and messengers can be intercepted. How can we ensure that all loyal generals reach the same decision? This military metaphor serves as a basis to illustrate the challenges faced by modern distributed systems.
The first work on this problem, conducted in the 1980s, laid the theoretical foundations for what would become a crucial field in modern computing. Leslie Lamport, a pioneer in this field, demonstrated that consensus was impossible to achieve deterministically in an asynchronous system if even a single node could fail.
Anatomy of a consensus
A robust consensus mechanism must guarantee several essential properties:
- All nodes deemed “honest” must converge on the same decision. This property is inviolable, even in case of network partition.
- The system must continue to progress and make decisions, even in the presence of failures or attacks.
- Once a decision is made, it cannot be questioned. This property exists in two forms: immediate finality and probabilistic finality. Immediate finality, found notably in BFT protocols like PBFT or Tendermint, guarantees that once a decision is validated by the network, it is final and absolutely cannot be questioned.
Take the example of a bank transaction: when your bank confirms that a transfer is complete, you want absolute certainty that this transaction will never be canceled or modified. This form of finality typically requires a multi-step validation process with explicit votes from participants, similar to how, for an important decision, all board members would need to sign an official document.
Probabilistic finality, used notably by Bitcoin and Proof of WorkProof of Work A consensus mechanism where miners compete to solve complex mathematical problems to validate transactions and secure the network.-based systems, works differently. In this case, the certainty that a decision is final gradually increases with time. Taking Bitcoin as an example, the more blocks confirmed after a transaction (known as “confirmations”), the more statistically unlikely it becomes for this transaction to be questioned. It’s like how confidence in a historical event increases with the number of independent sources confirming it. After six confirmations in Bitcoin (about one hour), the probability of seeing a transaction questioned becomes infinitely small, but is never theoretically zero.
Time and failure models
Distributed systems rely on different temporal models that modify their architecture and operation. In a synchronous model, the system guarantees that each message will be transmitted within a precise and known timeframe, which greatly facilitates protocol design but rarely proves feasible in the current context with Internet where transmission delays are unpredictable.

Conversely, the asynchronous model adopts an approach closer to reality by making no assumptions about message transmission delays, thus making protocol design more complex but more robust against real network uncertainties. Between these two extremes, the partially synchronous model offers a compromise by considering that the system can go through phases where it behaves synchronously or asynchronously, thus adapting to changing network conditions while allowing the design of efficient protocols.
Proof of Work: the Bitcoin revolution
PoW represents a major innovation as it solves the consensus problem in a completely open and hostile environment. Its operation relies on several subtle mechanisms:
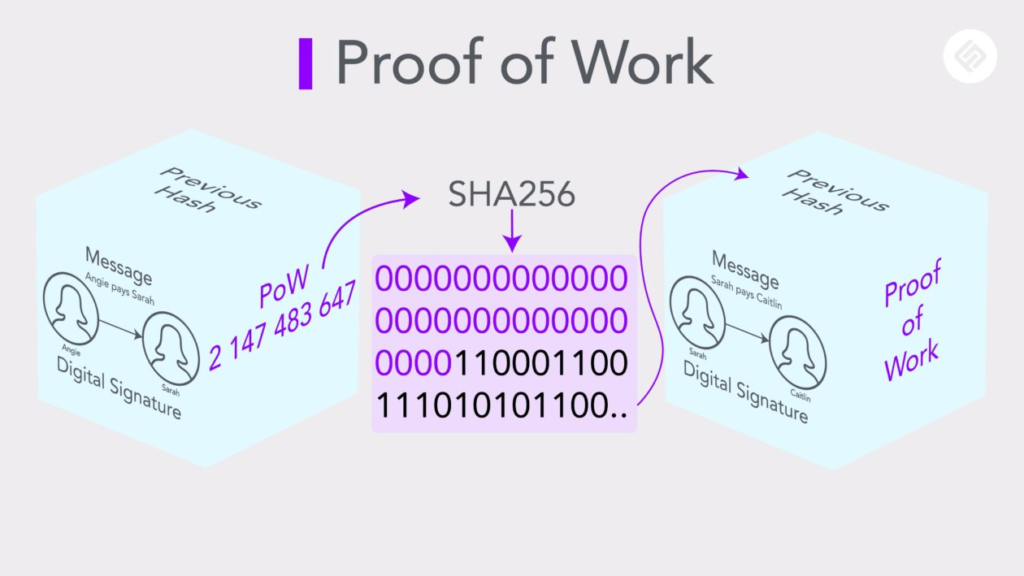
Proof of Work relies on three fundamental mechanisms that guarantee network securitySecurity The measures and technologies used to protect blockchain networks and assets from theft, fraud, and attacks. and stability. At the system’s core is a hashHash A cryptographic function that converts input data into a fixed-size alphanumeric string. function that must not only resist attacks but also present specific properties making it “puzzle-friendly” – SHA-256 used by Bitcoin is the perfect example. To maintain network regularity, an ingenious automatic difficulty adjustment system intervenes every 2016 blocks, allowing to maintain an average time of 10 minutes between each blockBlock A fundamental element of a blockchain, containing a set of transactions., regardless of the network’s total computing power. Also, to manage temporary divergences that occur in a decentralized network, the protocol applies the elegant longest chain rule, which allows the network to naturally converge towards consensus by favoring the chain representing the most cumulative work.
Proof of StakeProof of Stake A consensus mechanism where validators are selected based on the number of tokens they hold and are willing to "stake" as collateral., new paradigm
In a PoS system, validators are chosen to verify transactions and add new blocks to the blockchainBlockchain A public and immutable ledger of cryptographic transactions, organized in blocks. based on the quantity of tokens they have staked. The more tokens a participant has staked, the higher their chances of being selected. For example, in Ethereum 2.0, a validatorValidator A participant in a Proof of Stake network responsible for validating transactions and securing the network.A participant in a Proof of Stake network responsible for validating transactions and securing the network. must lock at least 32 ETH to participate in consensus. Once selected, the validator verifies block transactions and receives a reward in the form of new cryptocurrencies or transaction fees.
This process is automated by algorithms that select validators according to predefined criteria. These criteria typically include:
- The staked amount: The more tokens a user has locked, the higher their chances of being chosen.
- Seniority: Some systems favor validators who have been participating in the network for a long time.
- Randomization: To avoid excessive centralization, random elements are sometimes introduced in the selection process.
A concrete example is Tezos, where validators (called “bakers”) are chosen based on the number of Tezzies (XTZ) they hold and stake. Each validator receives a reward proportional to their commitment, which incentivizes both active participation and honest behavior.
To ensure network integrity, PoS incorporates a mechanism called “slashingSlashing A penalty mechanism in Proof of Stake networks where a portion of a validator's staked tokens is taken away for malicious behavior or failure to perform their duties.”. This penalizes validators who act maliciously or negligently. For example, if a validator attempts to add fraudulent transactions or remains inactive when they are supposed to validate a block, some or all of their staked tokens can be confiscated. This deterrent system strengthens network security by aligning participants’ economic interests with those of the system.
With Ethereum 2.0, where slashing is applied if a validator proposes multiple contradictory blocks or fails to fulfill their obligations, this ensures that only serious and honest participants remain involved in the process.
Modern BFT protocols
Protocols like Tendermint and Hotstuff have introduced significant optimizations in the consensus field. The principle of leader rotation periodically redistributes responsibilities among participants, thus strengthening system resilience. These protocols have also optimized communication by reducing the volume of necessary messages and allowing parallel processing of proposals, significantly improving overall network performance.
DeFiDeFi DeFi services use smart contracts, decentralized protocols, and tokens to offer a range of financial services that can sometimes replace those offered by banks, such as lending/borrowing, asset management, insurance, or asset exchange. requires particularly fast and fair consensus mechanisms. Transaction finality must be near-instantaneous while ensuring protection against manipulation. Protocols must operate efficiently with devices having limited resources and intermittent connections while maintaining their ability to scale to millions of nodes.
What future for consensus mechanisms?
Their evolution reflects our progression towards increasingly distributed and autonomous systems. Current challenges (scalabilityScalability The ability of a blockchain network to handle a growing number of transactions efficiently. and energy efficiency) stimulate continuous innovation in this field.
Research is moving towards hybrid and adaptive systems, capable of combining the advantages of different approaches depending on the context. This evolution could lead to a new generation of more efficient, secure, and sustainable distributed systems, thus shaping tomorrow’s digital infrastructure.











